- Tracked incidents are often classified into ready-made responses that are not necessarily applicable to the organization. With so many classifications, tracking becomes inefficient and indigestible, allowing major incidents to fall through the cracks.
- Outcomes of incident response tactics are not formally tracked or communicated, resulting in a lack of comprehensive understanding of trends and patterns regarding incidents, leading to being re-victimized by the same vector.
- Having a formal incident response document to meet compliance requirements is not useful if no one is adhering to it.
Our Advice
Critical Insight
- You will experience incidents. Don’t rely on ready-made responses. They’re too broad and easy to ignore. Save your organization response time and confusion by developing your own specific incident use cases.
- Analyze, track, and review results of incident response regularly. Without a comprehensive understanding of incident trends and patterns, you can be re-victimized by the same attack vector.
- Establish communication processes and channels well in advance of a crisis. Don’t wait until a state of panic. Collaborate and exchange information with other organizations to stay ahead of incoming threats.
Impact and Result
- Effective and efficient management of incidents involves a formal process of preparation, detection, analysis, containment, eradication, recovery, and post-incident activities.
- This blueprint will walk through the steps of developing a scalable and systematic incident response program relevant to your organization.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
9.2/10
Overall Impact
$109,866
Average $ Saved
40
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
The Corporation of the City of Sault Ste. Marie
Workshop
10/10
$75,000
110
CPA Alberta
Guided Implementation
8/10
$10,000
5
California Department of Housing & Community Development
Workshop
10/10
$129K
115
County of Franklin
Guided Implementation
10/10
$2,599
20
Kappa Delta Sorority
Guided Implementation
10/10
$12,999
60
Charlotte County Clerk of the Circuit Court and County Comptroller
Workshop
10/10
N/A
110
Osage Casinos
Guided Implementation
10/10
$14,949
20
RJRGLEANER Communications Group
Guided Implementation
9/10
N/A
26
Asian Development Bank
Guided Implementation
9/10
N/A
N/A
The Corporation of the City of Timmins
Guided Implementation
10/10
$10,000
20
Government of Bermuda
Workshop
8/10
$389K
110
New-Indy Containerboard, LLC
Guided Implementation
10/10
$2,469
9
Noramco, LLC
Guided Implementation
10/10
$59,849
10
Pekin Insurance
Workshop
9/10
$61,749
20
4Wall Entertainment
Workshop
10/10
$18,269
5
County Of Kenosha
Workshop
8/10
$12,999
20
ENERGYUNITED ELECTRIC MEMBERSHIP CORPORATION
Workshop
10/10
$1.3M
120
Healthcare Excellence Canada
Guided Implementation
8/10
N/A
5
Corix Infrastructure Inc.
Guided Implementation
10/10
$37,500
20
Afreximbank
Guided Implementation
8/10
$23,500
110
Jet Support Services, Inc.
Workshop
10/10
$12,599
20
The Regional Municipality Of Niagara
Workshop
7/10
N/A
50
Saskatchewan Blue Cross
Guided Implementation
8/10
N/A
5
Hyperloop Technologies, Inc.
Workshop
10/10
$37,199
20
Massey University
Workshop
8/10
$61,999
5
OSI Group LLC
Workshop
8/10
$30,999
20
City Of Greenwood Village
Guided Implementation
10/10
$2,519
10
Interdigital Communications
Workshop
9/10
N/A
N/A
First Hope Bank
Workshop
10/10
$12,399
18
PlayPower, Inc
Guided Implementation
9/10
$30,999
10
Workshop: Develop and Implement a Security Incident Management Program
Workshops offer an easy way to accelerate your project. If you are unable to do the project yourself, and a Guided Implementation isn't enough, we offer low-cost delivery of our project workshops. We take you through every phase of your project and ensure that you have a roadmap in place to complete your project successfully.
Module 1: Prepare Your Incident Response Program
The Purpose
- Understand the purpose of incident response.
- Formalize the program.
- Identify key players and escalation points.
Key Benefits Achieved
- Common understanding of the importance of incident response.
- Various business units becoming aware of their roles in the incident management program.
- Formalized documentation.
Activities
Outputs
Assess the current process, obligations, scope, and boundaries of the incident management program.
- Understanding of the incident landscape
Identify key players for the response team and for escalation points.
- An identified incident response team
Formalize documentation.
- A security incident management charter
- A security incident management policy
Prioritize incidents requiring preparation.
- A list of top-priority incidents
- A general security incident management plan
- A security incident response RACI chart
Module 2: Develop Incident-Specific Runbooks
The Purpose
- Document the clear response procedures for top-priority incidents.
Key Benefits Achieved
- As incidents occur, clear response procedures are documented for efficient and effective recovery.
Activities
Outputs
For each top-priority incident, document the workflow from detection through analysis, containment, eradication, recovery, and post-incident analysis.
- Up to five incident-specific runbooks
Module 3: Maintain and Optimize the Program
The Purpose
- Ensure the response procedures are realistic and effective.
- Identify key metrics to measure the success of the program.
Key Benefits Achieved
- Real-time run-through of security incidents to ensure roles and responsibilities are known.
- Understanding of how to measure the success of the program.
Activities
Outputs
Limited scope tabletop exercise.
- Completed tabletop exercise
Discuss key metrics.
- Key success metrics identified
Develop and Implement a Security Incident Management Program
Create a scalable incident response program without breaking the bank.
ANALYST PERSPECTIVE
Security incidents are going to happen whether you’re prepared or not. Ransomware and data breaches are just a few top-of-mind threats that all organizations deal with. Taking time upfront to formalize response plans can save you significantly more time and effort down the road. When an incident strikes, don’t waste time deciding how to remediate. Rather, proactively identify your response team, optimize your response procedures, and track metrics so you can be prepared to jump to action.
Céline Gravelines,
Senior Research Analyst
Security, Risk & Compliance Info-Tech Research Group

Céline Gravelines,
Senior Research Analyst
Security, Risk & Compliance Info-Tech Research Group
Our understanding of the problem
This Research is Designed For
- A CISO who is dealing with the following:
- Inefficient use of time and money when retroactively responding to incidents, negatively affecting business revenue and workflow.
- Resistance from management to adequately develop a formal incident response plan.
- Lack of closure of incidents, resulting in being re-victimized by the same vector.
This Research Will Help You
- Develop a consistent, scalable, and usable incident response program that is not resource intensive.
- Track and communicate incident response in a formal manner.
- Reduce the overall impact of incidents over time.
- Learn from past incidents to improve future response processes.
This Research Will Also Assist
- Business stakeholders who are responsible for the following:
- Improving workflow and managing operations in the event of security incidents to reduce any adverse business impacts.
- Ensuring that incident response compliance requirements are being adhered to.
This Research Will Help Them
- Efficiently allocate resources to improve incident response in terms of incident frequency, response time, and cost.
- Effectively communicate expectations and responsibilities to users.
Executive Summary
Situation
- Security incidents are inevitable, but how they’re dealt with can make or break an organization. Poor incident response negatively affects business practices, including workflow, revenue generation, and public image.
- The incident response of most organizations is ad hoc at best. A formal management plan is rarely developed or adhered to, resulting in ineffective firefighting responses and inefficient allocation of resources.
Complication
- Tracked incidents are often classified into ready-made responses that are not necessarily applicable to the organization. With so many classifications, tracking becomes inefficient and indigestible, allowing major incidents to fall through the cracks.
- Outcomes of incident response tactics are not formally tracked or communicated, resulting in a lack of comprehensive understanding of trends and patterns regarding incidents, leading to being revictimized by the same vector.
- Having a formal incident response document to meet compliance requirements is not useful if no one is adhering to it.
Resolution
- Effective and efficient management of incidents involves a formal process of preparation, detection, analysis, containment, eradication, recovery, and post-incident activities.
- This blueprint will walk through the steps of developing a scalable and systematic incident response program relevant to your organization.
Info-Tech Insight
- You will experience incidents. Don’t rely on ready-made responses. They’re too broad and easy to ignore. Save your organization response time and confusion by developing your own specific incident use cases.
- Analyze, track, and review results of incident response regularly. Without a comprehensive understanding of incident trends and patterns, you can be re-victimized by the same attack vector.
- Establish communication processes and channels well in advance of a crisis. Don’t wait until a state of panic. Collaborate and exchange information with other organizations to stay ahead of incoming threats.
Data breaches are resulting in major costs across industries
Per capita cost by industry classification of benchmarked companies (measured in USD)
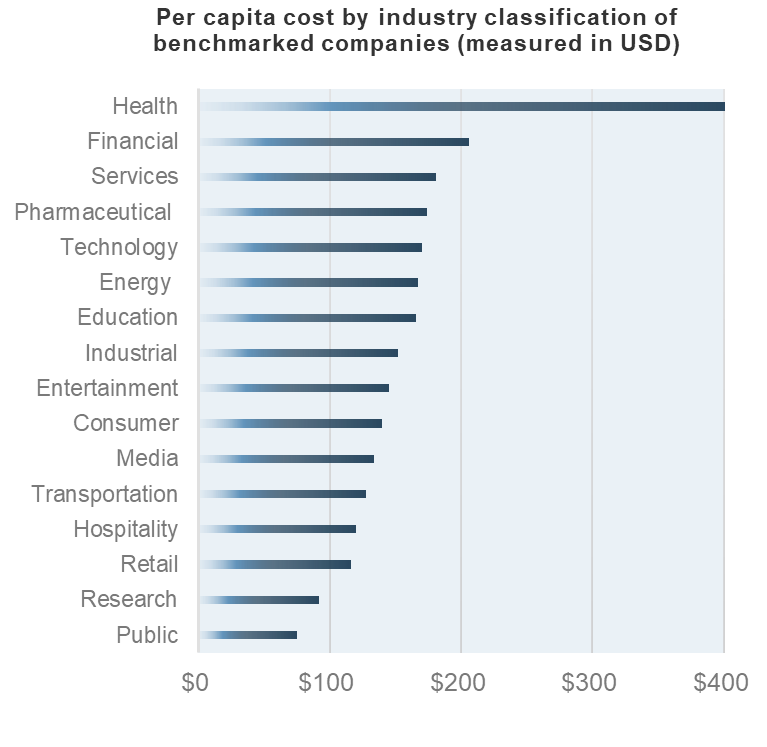
Average data breach costs per compromised record hit an all-time high of $148 (in 2018).
(Source: IBM, “2018 Cost of Data Breach Study)”
| % of systems impacted by a data breach | ||||
|---|---|---|---|---|
| 1% No Impact |
19% 1-10% impacted |
41% 11-30% impacted |
24% 31-50% impacted |
15% > 50% impacted |
| % of customers lost from a data breach | ||||
| 61% Lost < 20% |
21% Lost 20-40% | 8% Lost 40-60% |
6% Lost 60-80% |
4% Lost 80-100% |
| % of customers lost from a data breach | ||||
| 58% Lost <20% |
25% Lost 20-40% |
9% Lost 40-60% |
5% Lost 60-80% |
4% Lost 80-100% |
Source: Cisco, “Cisco 2017 Annual Cybersecurity Report”
Defining what is security incident management
IT Incident
Any event not a part of the standard operation of a service which causes, or may cause, the interruption to, or a reduction in, the quality of that service.
Security Event:
A security event is anything that happens that could potentially have information security implications.
- A spam email is a security event because it may contain links to malware.
- Organizations may be hit with thousands or perhaps millions of identifiable security events each day.
- These are typically handled by automated tools or are simply logged.
Security Incident:
A security incident is a security event that results in damage such as lost data.
- Incidents can also include events that don't involve damage but are viable risks.
- For example, an employee clicking on a link in a spam email that made it through filters may be viewed as an incident.
It’s not a matter of if you have a security incident, but when
The increasing complexity and prevalence of threats have finally caught the attention of corporate leaders. Prepare for the inevitable with an incident response program.
- A formalized incident response program reduced the average cost of a data breach (per capita) from $148 to $134, while third-party involvement increased costs by $13.40.
- US organizations lost an average of $7.91 million per data breach as a result of increased customer attrition and diminished goodwill. Canada and the UK follow suit at $1.57 and $1.39 million, respectively.
- 73% of breaches are perpetrated by outsiders, 50% are the work of criminal groups, and 28% involve internal actors.
- 55% of companies have to manage fallout, such as reputational damage after a data breach.
- The average cost of a data breach increases by $1 million if left undetected for > 100 days.
(Sources: IBM, “2018 Cost of Data Breach Study”; Verizon, “2017 Data Breach Investigations Report”; Cisco, “Cisco 2018 Annual Cybersecurity Report”)
Threat Actor Examples
The proliferation of hacking techniques and commoditization of hacking tools has enabled more people to become threat actors. Examples include:- Organized Crime Groups
- Lone Cyber Criminals
- Competitors
- Nation States
- Hacktivists
- Terrorists
- Former Employees
- Domestic Intelligence Services
- Current Employees (malicious and accidental)
Benefits of an incident management program
Effective incident management will help you do the following:
Improve efficacy
Develop structured processes to increase process consistency across the incident response team and the program as a whole. Expose operational weak points and transition teams from firefighting to innovating.
Improve threat detection, prevention, analysis, and response
Enhance your pressure posture through a structured and intelligence-driven incident handling and remediation framework.
Improve visibility and information sharing
Promote both internal and external information sharing to enable good decision making.
Create and clarify accountability and responsibility
Establish a clear level of accountability throughout the incident response program, and ensure role responsibility for all tasks and processes involved in service delivery.
Control security costs
Effective incident management operations will provide visibility into your remediation processes, enabling cost savings from misdiagnosed issues and incident reduction.
Identify opportunities for continuous improvement
Increase visibility into current performance levels and accurately identify opportunities for continuous improvement with a holistic measurement program.
Impact
Short term:- Streamlined security incident management program.
- Formalized and structured response process.
- Comprehensive list of operational gaps and initiatives.
- Detailed response runbooks that predefine necessary operational protocol.
- Compliance and audit adherence.
- Reduced incident costs and remediation time.
- Increased operational collaboration between prevention, detection, analysis, and response efforts.
- Enhanced security pressure posture.
- Improved communication with executives about relevant security risks to the business.
- Preserved reputation and brand equity.
Incident management is essential for organizations of any size
Your incidents may differ, but a standard response ensures practical security.
Certain regulations and laws require incident response to be a mandatory process in organizations.
| Compliance Standard Examples | Description |
|---|---|
| Federal Information Security Modernization Act (FISMA) |
|
| Federal Information Processing Standards (FIPS) |
|
| Payment Card Industry Data Security Standard (PCI DSS v3) |
|
| Health Insurance Portability and Accountability Act (HIPAA) |
|
Security incident management is applicable to all verticals
Examples:- Finance
- Insurance
- Healthcare
- Public administration
- Education services
- Professional services
- Scientific and technical services
Maintain a holistic security operations program
Legacy security operations centers (SOCs) fail to address gaps between data sources, network controls, and human capital. There is limited visibility and collaboration between departments, resulting in siloed decisions that do not support the best interests of the organization.

Security operations is part of what Info-Tech calls a threat collaboration environment, where members must actively collaborate to address cyberthreats affecting the organization’s brand, business operation, and technology infrastructure on a daily basis.
| Prevent: Defense in depth is the best approach to protect against unknown and unpredictable attacks. Diligent patching and vulnerability management, endpoint protection, and strong human-centric security (amongst other tactics) are essential. | Detect: There are two types of companies – those who have been breached and know it, and those who have been breached and don’t know it. Ensure that monitoring, logging, and event detection tools are in place and appropriate to your organizational needs. |
| Analyze: Raw data without interpretation cannot improve security and is a waste of time, money, and effort. Establish a tiered operational process that not only enriches data but also provides visibility into your threat landscape. | Respond: Organizations can’t rely on an ad hoc response anymore – don’t wait until a state of panic. Formalize your response processes in a detailed incident runbook to reduce incident remediation time and effort. |
Info-Tech’s incident response blueprint is one of four security operations initiatives
| Design and Implement a Vulnerability Management Program | Vulnerability Management Vulnerability management revolves around the identification, prioritization, and remediation of vulnerabilities. Vulnerability management teams hunt to identify which vulnerabilities need patching and remediating. |
|
| Integrate Threat Intelligence Into Your Security Operations | Vulnerability Management Vulnerability management revolves around the identification, prioritization, and remediation of vulnerabilities. Vulnerability management teams hunt to identify which vulnerabilities need patching and remediating. |
|
| Develop Foundational Security Operations Processes | Operations Security operations include the real-time monitoring and analysis of events based on the correlation of internal and external data sources. This also includes incident escalation based on impact. These analysts are constantly tuning and tweaking rules and reporting thresholds to further help identify which indicators are most impactful during the analysis phase of operations. |
|
| Develop and Implement a Security Incident Management Program | Incident Response (IR) Effective and efficient management of incidents involves a formal process of analysis, containment, eradication, recovery, and post-incident activities. Incident response teams coordinate root cause and incident gathering while facilitating post-incident lessons learned. Incident response can provide valuable threat data that ties specific indicators to threat actors or campaigns. |
Security Incident Management Policy
|
|---|
Understand how incident response ties into related processes
| Info-Tech Resources: | |
|---|---|
| Business Continuity Plan | Develop a Business Continuity Plan |
| Disaster Recovery Plan | Create a Right-Sized Disaster Recovery Plan |
| Security Incident Management | Develop and Implement a Security Incident Management Program |
| Incident Management | Incident and Problem Management |
| Service Desk | Standardize the Service Desk |
Develop and Implement a Security Incident Management Program – project overview
| 1. Prepare | 2. Operate | 3. Maintain and Optimize | |
|---|---|---|---|
| Best-Practice Toolkit | 1.1 Establish the Drivers, Challenges, and Benefits. 1.2 Examine the Security Incident Landscape and Trends. 1.3 Understand Your Security Obligations, Scope, and Boundaries. 1.4 Gauge Your Current Process to Identify Gaps. 1.5 Formalize the Security Incident Management Charter. 1.6 Identify Key Players and Develop a Call Escalation Tree. 1.7 Develop a Security Incident Management Policy. |
2.1 Understand the Incident Response Framework. 2.2 Understand the Purpose of Runbooks. 2.3 Prioritize the Development of Incident-Specific Runbooks. 2.4 Develop Top-Priority Runbooks. 2.5 Fill Out the Root-Cause Analysis Template. 2.6 Customize the Post-Incident Review Questions Tracking Tool to Standardize Useful Questions for Lessons-Learned Meetings. 2.7 Complete the Security Incident Report Template. |
3.1 Conduct Tabletop Exercises. 3.2 Initialize a Security Incident Management Metrics Program. 3.3 Leverage Best Practices for Continuous Improvement. |
| Guided Implementations | Understand the incident response process, and define your security obligations, scope, and boundaries. Formalize the incident management charter, RACI, and incident management policy. |
Use the framework to develop a general incident management plan. Prioritize and develop top-priority runbooks. |
Develop and facilitate tabletop exercises. Create an incident management metrics program, and assess the success of the incident management program. |
| Onsite Workshop | Module 1: Prepare for Incident Response |
Module 2: Handle Incidents |
Module 3: Review and Communicate Security Incidents |
| Phase 1 Outcome:
|
Phase 2 Outcome:
|
Phase 3 Outcome:
|
Workshop overview
Contact your account representative or email Workshops@InfoTech.com for more information.
| Workshop Day 1 | Workshop Day 2 | Workshop Day 3 | Workshop Day 4 | Workshop Day 5 | |
|---|---|---|---|---|---|
| Activities |
|
|
|
|
|
| Deliverables |
|
|
|
|
|
Measured value for Guided Implementations
Engaging in GIs doesn’t just offer valuable project advice – it also results in significant cost savings.
| GI | Purpose | Measured Value |
|---|---|---|
| Section 1: Prepare |
Understand the need for an incident response program. |
Time, value, and resources saved using our classification guidance and templates:
2 FTEs*2 days*$80,000/year =
$1,280 |
| Section 2: Operate |
Prioritize runbooks and develop the processes to create your own incident response program: |
Time, value, and resources saved using our guidance: 1 consultant*15 days*$2,000/day = $30,000 (if done by third party) |
| Section 3: Maintain and Optimize | Develop methods of proper reporting and create templates for communicating incident response to key parties. | Time, value, and resources saved using our guidance, templates, and tabletop exercises: 2 FTEs*3 days*$80,000/year = $1,920 |
| Total Costs | To just get an incident response program off the ground. | $49,200 |
Insurance company put incident response aside; executives were unhappy
Organization implemented ITIL, but formal program design became less of a priority and turned more ad hoc.
Situation
- Ad hoc processes created management dissatisfaction around the organization’s ineffective responses to data breaches.
- Because of the lack of formal process, an entirely new security team needed to be developed, costing people their positions.
Challenges
- Lack of criteria to categorize and classify security incidents.
- Need to overhaul the long-standing but ineffective program means attempting to change mindsets, which can be time consuming.
- Help desk is not very knowledgeable on security.
- New incident response program needs to be in alignment with data classification policy and business continuity.
- Lack of integration with MSSP’s ticketing system.
Next steps:
- Need to get stakeholder buy-in for a new program.
- Begin to establish classification/reporting procedures.
Follow this case study to Phase 1
Phase 1
Prepare
Develop and Implement a Security Incident Management Program
Phase 1: Prepare
| PHASE 1 | PHASE 2 | PHASE 3 |
|---|---|---|
| Prepare | Operate | Optimize |
This phase walks you through the following activities:
1.1 Establish the drivers, challenges, and benefits.
1.2 Examine the security incident landscape and trends.
1.3 Understand your security obligations, scope, and boundaries.
1.4 Gauge your current process to identify gaps.
1.5 Formalize a security incident management charter.
1.6 Identify key players and develop a call escalation tree.
1.7 Develop a security incident management policy.
This phase involves the following participants:
- CISO
- Security team
- IT staff
- Business leaders
Outcomes of this phase
- Formalized stakeholder support.
- Security incident management policy.
- Security incident management charter.
- Call escalation tree.
Phase 1 outline
Call 1-888-670-8889 or email GuidedImplementations@InfoTech.com for more information.
Complete these steps on your own, or call us to complete a guided implementation. A guided implementation is a series of 2-3 advisory calls that help you execute each phase of a project. They are included in most advisory memberships.
| Guided Implementation 1: Prepare for Incident Response Proposed Time to Completion: 3 Weeks |
|
|---|---|
| Step 1.1-1.3 Understand Incident Response | Step 1.4-1.7 Begin Developing Your Program |
| Start with an analyst kick-off call:
|
Review findings with analyst:
|
Then complete these activities…
|
Then complete these activities…
|
|
With these tools & templates: |
With these tools & templates: Security Incident Management Policy Security Incident Management Plan |
|
Phase 1 Results & Insights: Ready-made incident response solutions often contain too much coverage: too many irrelevant cases that are not applicable to the organization are accounted for, making it difficult to sift through all the incidents to find the ones you care about. Develop specific incident use cases that correspond with relevant incidents to quickly identify the response process and eliminate ambiguity when handled by different individuals. |
|
Ice breaker: What is a security incident for your organization?
1.1 Whiteboard Exercise – 60 minutes
How do you classify various incident types between service desk, IT/infrastructure, and security?
- Populate sticky notes with various incidents and assign them to the appropriate team.
- Who owns the remediation? When are other groups involved? What is the triage/escalation process?
- What other groups need to be notified (e.g. cyber insurance, Legal, HR, PR)?
- Are there dependencies among incidents?
- What are we covering in the scope of this project?
 Develop and Implement a Security Incident Management Program
Develop and Implement a Security Incident Management Program
 Build Resilience Against Ransomware Attacks
Build Resilience Against Ransomware Attacks
 Build a Vendor Security Assessment Service
Build a Vendor Security Assessment Service
 Implement Risk-Based Vulnerability Management
Implement Risk-Based Vulnerability Management
 Design a Tabletop Exercise to Support Your Security Operation
Design a Tabletop Exercise to Support Your Security Operation
 Integrate Threat Intelligence Into Your Security Operations
Integrate Threat Intelligence Into Your Security Operations
 Master Your Security Incident Response Communications Program
Master Your Security Incident Response Communications Program
 Design a Coordinated Vulnerability Disclosure Program
Design a Coordinated Vulnerability Disclosure Program