- Companies are aware of the need to discuss and assess risk, but many struggle to do so in a systematic and repeatable way.
- Rarely are security risks analyzed in a consistent manner, let alone in a systematic and repeatable method to determine project risk as well as overall organizational risk exposure.
Our Advice
Critical Insight
- The best security programs are built upon defensible risk management. With an appropriate risk management program in place, you can ensure that security decisions are made strategically instead of based on frameworks and gut feelings. This will optimize any security planning and budgeting.
- All risks can be quantified. Security, compliance, legal, or other risks can be quantified using our methodology.
Impact and Result
- Develop a security risk management program to create a standardized methodology for assessing and managing the risk that information systems face.
- Build a risk governance structure that makes it clear how security risks can be escalated within the organization and who makes the final decision on certain risks.
- Use Info-Tech’s risk assessment methodology to quantifiably evaluate the threat severity for any new or existing project or initiative.
- Tie together all aspects of your risk management program, including your information security risk tolerance level, threat and risk assessments, and mitigation effectiveness models.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
9.0/10
Overall Impact
$40,617
Average $ Saved
32
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
AgHeritage Farm Credit Services d/b/a Insight Technology Unit (ITU)
Workshop
8/10
$30,549
10
UCLA
Workshop
5/10
N/A
N/A
Diamond Trading Company Botswana (PTY) LTD.
Workshop
10/10
$12,999
10
UCLA
Workshop
9/10
N/A
32
UCLA
Workshop
10/10
$64,999
20
Camosun College
Guided Implementation
10/10
$25,000
20
California Department of Human Resources
Guided Implementation
10/10
$113K
115
American Transmission Company
Guided Implementation
8/10
$2,393
5
STERIS Corporation
Guided Implementation
10/10
$12,599
29
State of Hawaii – ETS
Guided Implementation
10/10
$62,999
50
London Health Sciences Centre and St. Joseph’s Health Care, London
Guided Implementation
9/10
$10,000
5
Southwest Gas Corporation
Guided Implementation
10/10
$125K
20
Atlantic Canada Opportunities Agencies
Guided Implementation
8/10
$47,500
10
Canadian National Railway
Guided Implementation
10/10
$2,000
5
Blessing Hospital
Guided Implementation
8/10
N/A
N/A
Blessing Hospital
Guided Implementation
10/10
N/A
N/A
California Department of Corrections & Rehabilitation
Guided Implementation
9/10
N/A
N/A
Federal Home Loan Bank of Chicago
Guided Implementation
10/10
N/A
N/A
Nakisa Inc.
Workshop
8/10
N/A
20
The Ottawa Hospital
Guided Implementation
10/10
$11,500
10
British Columbia Transit
Workshop
8/10
$50,000
20
California Department of Corrections & Rehabilitation
Guided Implementation
9/10
N/A
N/A
Apria Healthcare
Guided Implementation
8/10
N/A
N/A
Colonial Savings, F.A.
Guided Implementation
10/10
$764K
10
BWX TECHNOLOGIES, INC.
Guided Implementation
9/10
N/A
N/A
Workshop: Combine Security Risk Management Components Into One Program
Workshops offer an easy way to accelerate your project. If you are unable to do the project yourself, and a Guided Implementation isn't enough, we offer low-cost delivery of our project workshops. We take you through every phase of your project and ensure that you have a roadmap in place to complete your project successfully.
Module 1: Establish the Risk Environment
The Purpose
- Build the foundation needed for a security risk management program.
- Define roles and responsibilities of the risk executive.
- Define an information security risk tolerance level.
Key Benefits Achieved
- Clearly defined roles and responsibilities.
- Defined risk tolerance level.
Activities
Outputs
Define the security executive function RACI chart.
- Defined risk executive functions
Assess business context for security risk management.
- Risk governance RACI chart
Standardize risk terminology assumptions.
- Defined quantified risk tolerance and risk factor weightings
Conduct preliminary evaluation of risk scenarios to determine your risk tolerance level.
Decide on a custom risk factor weighting.
Finalize the risk tolerance level.
Begin threat and risk assessment.
Module 2: Conduct Threat and Risk Assessments
The Purpose
- Determine when and how to conduct threat and risk assessments (TRAs).
- Complete one or two TRAs, as time permits during the workshop.
Key Benefits Achieved
- Developed process for how to conduct threat and risk assessments.
- Deep risk analysis for one or two IT projects/initiatives.
Activities
Outputs
Determine when to initiate a risk assessment.
Review appropriate data classification scheme.
Identify system elements and perform data discovery.
- Define scope of system elements and data within assessment
Map data types to the elements.
- Mapping of data to different system elements
Identify STRIDE threats and assess risk factors.
- Threat identification and associated risk severity
Determine risk actions taking place and assign countermeasures.
- Defined risk actions to take place in threat and risk assessment process
Calculate mitigated risk severity based on actions.
If necessary, revisit risk tolerance.
Document threat and risk assessment methodology.
Module 3: Continue to Conduct Threat and Risk Assessments
The Purpose
Complete one or two TRAs, as time permits during the workshop.
Key Benefits Achieved
Deep risk analysis for one or two IT projects/initiatives, as time permits.
Activities
Outputs
Continue threat and risk assessment activities.
As time permits, one to two threat and risk assessment activities will be performed as part of the workshop.
- One to two threat and risk assessment activities performed
Review risk assessment results and compare to risk tolerance level.
- Validation of the risk tolerance level
Module 4: Establish a Risk Register and Communicate Risk
The Purpose
- Collect, analyze, and aggregate all individual risks into the security risk register.
- Plan for the future of risk management.
Key Benefits Achieved
- Established risk register to provide overview of the organizational aggregate risk profile.
- Ability to communicate risk to other stakeholders as needed.
Activities
Outputs
Begin building a risk register.
- Risk register, with an inventory of risks and a macro view of the organization’s risk
Identify individual risks and threats that exist in the organization.
Decide risk responses, depending on the risk level as it relates to the risk tolerance.
If necessary, revisit risk tolerance.
Identify which stakeholders sign off on each risk.
Plan for the future of risk management.
- Defined risk-based initiatives to complete
Determine how to present risk to senior management.
- Plan for securing and managing the risk register
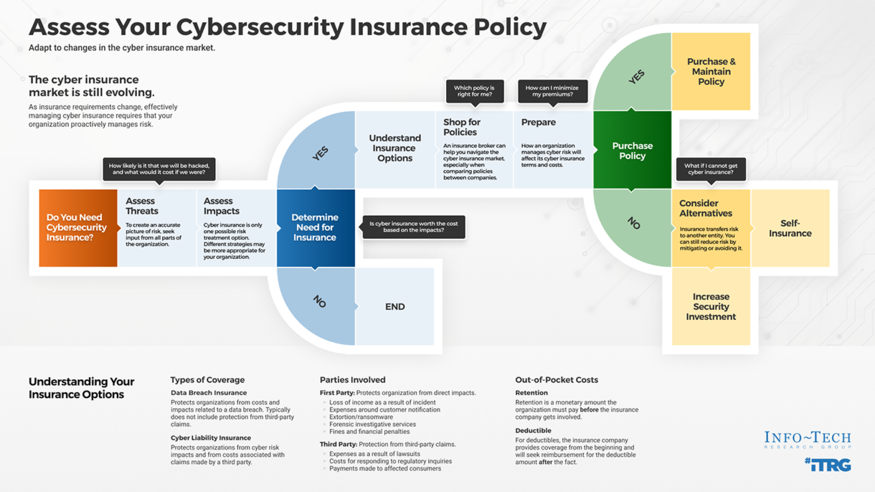 Assess Your Cybersecurity Insurance Policy
Assess Your Cybersecurity Insurance Policy
 Achieve Digital Resilience by Managing Digital Risk
Achieve Digital Resilience by Managing Digital Risk
 Combine Security Risk Management Components Into One Program
Combine Security Risk Management Components Into One Program
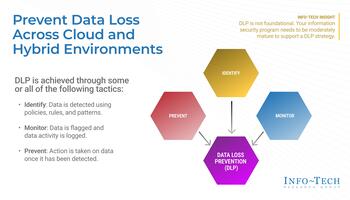 Prevent Data Loss Across Cloud and Hybrid Environments
Prevent Data Loss Across Cloud and Hybrid Environments
 Build an IT Risk Management Program
Build an IT Risk Management Program
 Close the InfoSec Skills Gap: Develop a Technical Skills Sourcing Plan
Close the InfoSec Skills Gap: Develop a Technical Skills Sourcing Plan
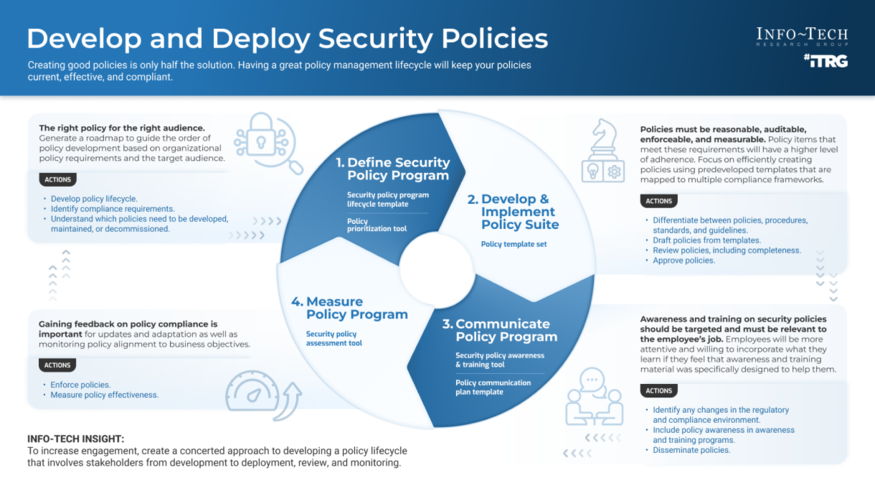 Develop and Deploy Security Policies
Develop and Deploy Security Policies
 Fast Track Your GDPR Compliance Efforts
Fast Track Your GDPR Compliance Efforts
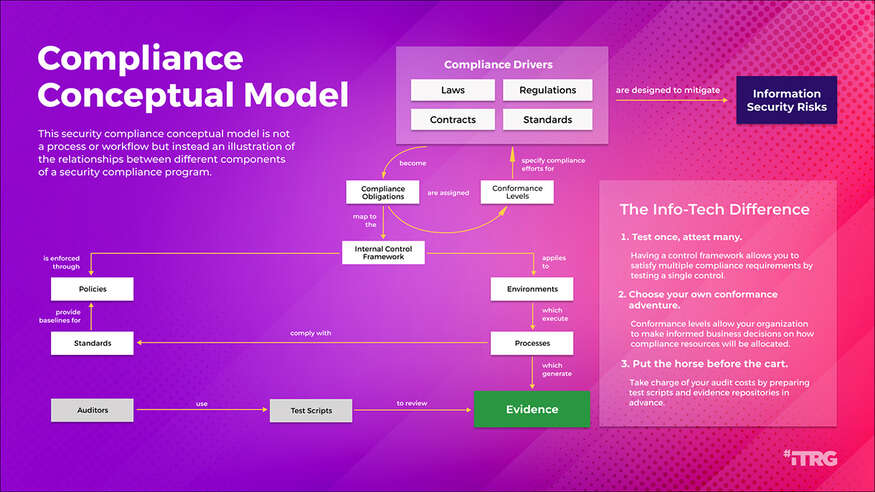 Build a Security Compliance Program
Build a Security Compliance Program
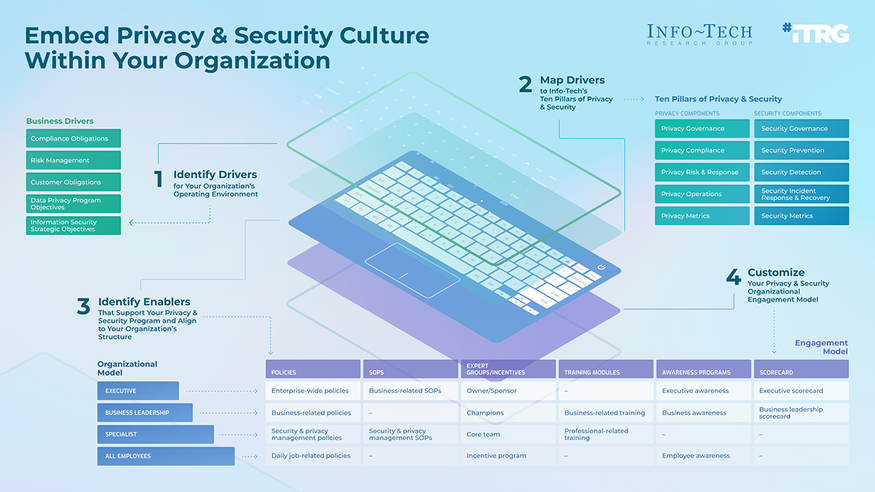 Embed Privacy and Security Culture Within Your Organization
Embed Privacy and Security Culture Within Your Organization
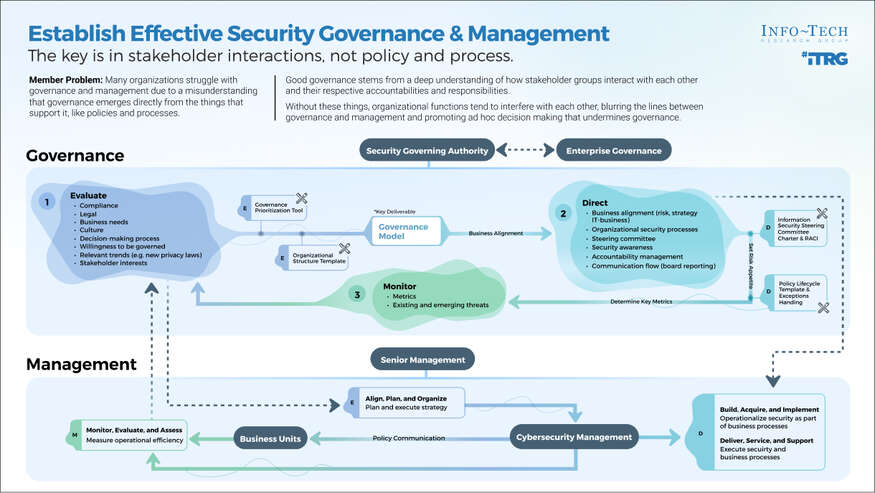 Establish Effective Security Governance & Management
Establish Effective Security Governance & Management
 Improve Security Governance With a Security Steering Committee
Improve Security Governance With a Security Steering Committee
 Develop Necessary Documentation for GDPR Compliance
Develop Necessary Documentation for GDPR Compliance
 Reduce and Manage Your Organization’s Insider Threat Risk
Reduce and Manage Your Organization’s Insider Threat Risk
 Satisfy Customer Requirements for Information Security
Satisfy Customer Requirements for Information Security
 Time Study
Time Study
 Responsibly Resume IT Operations in the Office
Responsibly Resume IT Operations in the Office
 Master M&A Cybersecurity Due Diligence
Master M&A Cybersecurity Due Diligence
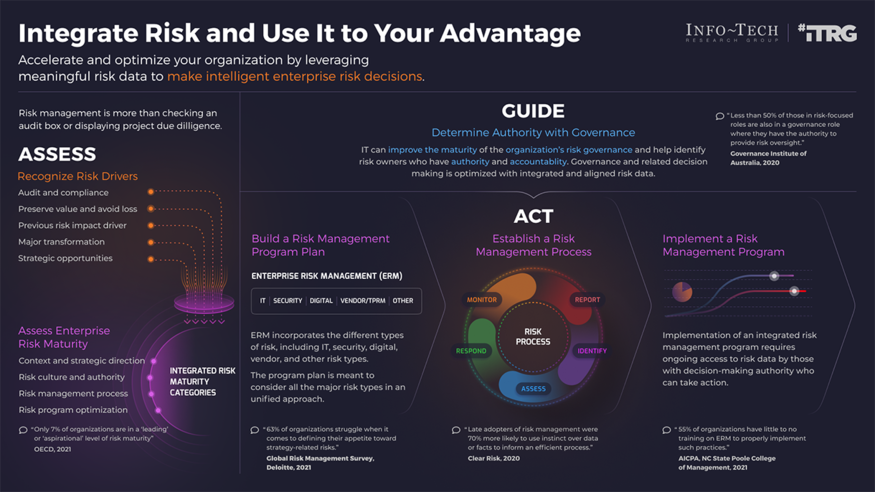 Integrate IT Risk Into Enterprise Risk
Integrate IT Risk Into Enterprise Risk
 Present Security to Executive Stakeholders
Present Security to Executive Stakeholders
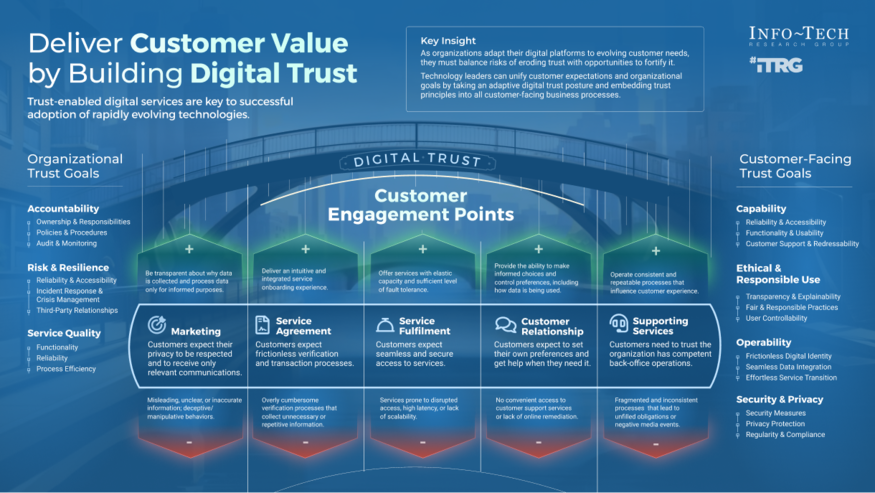 Deliver Customer Value by Building Digital Trust
Deliver Customer Value by Building Digital Trust