- Many security leaders struggle to decide how to best to prioritize their scarce information security resources
- The need to move from a reactive approach to security towards a strategic planning approach is clear. The path to getting there is less so.
Our Advice
Critical Insight
The most successful information security strategies are:
- Holistic – They consider the full spectrum of information security, including people, processes, and technology.
- Risk aware – They understand that security decisions should be made based on the security risks facing their organization, not just on “best practice.”
- Business aligned – They demonstrate an understanding of the goals and strategies of the organization and how the security program can support the business.
Impact and Result
- Info-Tech has developed a highly effective approach to building an information security strategy, an approach that has been successfully tested and refined for more than seven years with hundreds of different organizations:
- This approach includes tools for:
- Ensuring alignment with business objectives.
- Assessing organizational risk and stakeholder expectations.
- Enabling a comprehensive current state assessment.
- Prioritizing initiatives and building out a security roadmap.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
9.6/10
Overall Impact
$45,577
Average $ Saved
33
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
HSS Enterprises Ltd c/o IKO
Guided Implementation
10/10
$10,000
20
South Carolina Department of Employment and Workforce
Guided Implementation
10/10
N/A
4
American National Insurance Company Inc
Workshop
10/10
$12,999
10
St. Mary's University
Guided Implementation
10/10
$32,499
120
Worldnet International
Guided Implementation
10/10
$129K
50
IHC New Zealand Incorporated
Guided Implementation
9/10
$28,599
9
PrizePicks
Guided Implementation
10/10
$32,499
5
County of Nevada
Guided Implementation
9/10
N/A
5
City of O'Fallon
Guided Implementation
10/10
N/A
120
Sioux Lookout Meno Ya Win Health Centre
Guided Implementation
9/10
$20,500
20
SCEE
Guided Implementation
10/10
$21,499
50
AHF Products
Guided Implementation
8/10
$9,099
10
County of San Luis Obispo
Workshop
9/10
$32,499
10
Ministry of Industry, Innovation, Science and Technology
Workshop
9/10
$129K
50
Ausenco Engineering Canada Inc
Guided Implementation
10/10
$30,000
32
ATS CORPORATION
Guided Implementation
10/10
$10,000
20
Virginia Department of Health
Guided Implementation
10/10
N/A
115
Donor Network West
Guided Implementation
10/10
$32,499
10
Unity Health Care
Guided Implementation
10/10
$24,699
120
Loomis AB
Guided Implementation
10/10
$32,499
20
Government of Bermuda
Guided Implementation
10/10
$12,999
20
Canopy Growth
Guided Implementation
10/10
$17,500
10
Opentech Alliance
Guided Implementation
10/10
$779K
120
Matanuska-Susitna County
Guided Implementation
10/10
$25,000
20
Kentucky Public Pensions Authority
Workshop
9/10
N/A
10
Alabama Department of Economic and Community Affairs
Guided Implementation
10/10
$2,599
50
City of Saskatoon, SK
Workshop
10/10
$50,000
90
Power and Water Corporation
Guided Implementation
10/10
$42,999
18
ReCor Medical
Guided Implementation
10/10
N/A
N/A
Airgain
Guided Implementation
10/10
$129K
50

Security Strategy
Note: This course will be updated in August 2023.
Tailor best practices to effectively manage information security.
This course makes up part of the Security & Risk Certificate.
- Course Modules: 5
- Estimated Completion Time: 2-2.5 hours
- Featured Analysts:
- Kevin Peuhkurinen, Research Director, Security & Risk
- Gord Harrison, Senior Vice President, Research
Workshop: Build an Information Security Strategy
Workshops offer an easy way to accelerate your project. If you are unable to do the project yourself, and a Guided Implementation isn't enough, we offer low-cost delivery of our project workshops. We take you through every phase of your project and ensure that you have a roadmap in place to complete your project successfully.
Module 1: Assess Security Requirements
The Purpose
Understand business and IT strategy and plans.
Key Benefits Achieved
Defined security obligations, scope, and boundaries.
Activities
Outputs
Define business and compliance.
- Security obligations statement
Establish security program scope.
- Security scope and boundaries statement
Analyze the organization’s risk and stakeholder pressures.
- Defined risk tolerance level
Identify the organizational risk tolerance level.
- Risk assessment and pressure analysis
Module 2: Perform a Gap Analysis
The Purpose
Define the information security target state.
Key Benefits Achieved
Set goals and Initiatives for the security strategy in line with the business objectives.
Activities
Outputs
Assess current security capabilities.
- Information security target state
Identify security gaps.
- Security current state assessment
Build initiatives to bridge the gaps.
- Initiatives to address gaps
Module 3: Complete the Gap Analysis
The Purpose
Continue assessing current security capabilities.
Key Benefits Achieved
Identification of security gaps and initiatives to bridge them according to the business goals.
Activities
Outputs
Identify security gaps.
- Completed security current state assessment
Build initiatives to bridge the maturity gaps.
- Task list to address gaps
Identify initiative list and task list.
- Initiative list to address gaps
Define criteria to be used to prioritize initiatives.
- Prioritize criteria
Module 4: Develop the Roadmap
The Purpose
Create a plan for your security strategy going forward.
Key Benefits Achieved
Set path forward to achieving the target state for the business through goal cascade and gap initiatives.
Activities
Outputs
Conduct cost/benefit analysis on initiatives.
- Information security roadmap
Prioritize gap initiatives based on cost and alignment with business.
- Draft communication deck
Build an effort list.
Determine state times and accountability.
Finalize security roadmap and action plan.
Create communication plan.
Module 5: Communicate and Implement
The Purpose
Finalize deliverables.
Key Benefits Achieved
Consolidate documentation into a finalized deliverable that can be used to present to executives and decision makers to achieve buy-in for the project.
Activities
Outputs
Support communication efforts.
- Security strategy roadmap documentation
Identify resources in support of priority initiatives.
- Detailed cost and effort estimates
- Mapping of Info-Tech resources against individual initiatives
Build an Information Security Strategy
Create value by aligning your strategy to business goals and business risks.
Analyst Perspective
Set your security strategy up for success.
“Today’s rapid pace of change in business innovation and digital transformation is a call to action to information security leaders.
Too often, chief information security officers find their programs stuck in reactive mode, a result of years of mounting security technical debt. Shifting from a reactive to proactive stance has never been more important. Unfortunately, doing so remains a daunting task for many.
While easy to develop, security plans premised on the need to blindly follow ‘best practices’ are unlikely to win over many stakeholders. To be truly successful, an information security strategy needs to be holistic, risk-aware, and business-aligned.”
Kevin Peuhkurinen
Research Director – Security, Risk & Compliance
Info-Tech Research Group
Executive summary
Your Challenge
- Many security leaders struggle to decide how best to prioritize their scarce information security resources.
- The need to move from a reactive approach to security toward a strategic planning approach is clear. The path to getting there is less clear.
Common Obstacle
- Developing a security strategy can be challenging. Complications include:
- Performing an accurate assessment of your current security program can be extremely difficult when you don’t know what to assess or how.
- Determining the appropriate target state for security can be even more challenging. A strategy built around following best practices is unlikely to garner significant support from business stakeholders.
Info-Tech’s Approach
- Info-Tech has developed a highly effective approach to building an information security strategy, an approach that has been successfully tested and refined for 7+ years with hundreds of organizations.
- This unique approach includes tools for:
- Ensuring alignment with business objectives.
- Assessing organizational risk and stakeholder expectations.
- Enabling a comprehensive current state assessment.
- Prioritizing initiatives and building out a security roadmap.
Info-Tech Insight
The most successful information security strategies are:
- Holistic. They consider the full spectrum of information security, including people, processes, and technologies.
- Risk-Aware. They understand that security decisions should be made based on the security risks facing their organization, not just on best practice.
- Business-Aligned. They demonstrate an understanding of the goals and strategies of the organization, and how the security program can support the business.
It’s not a matter of if you have a security incident, but when
Organizations need to prepare and expect the inevitable security breach.
Fifty-eight percent of companies surveyed that experienced a breach were small businesses.
Eighty-nine percent of breaches have a financial or espionage motive.
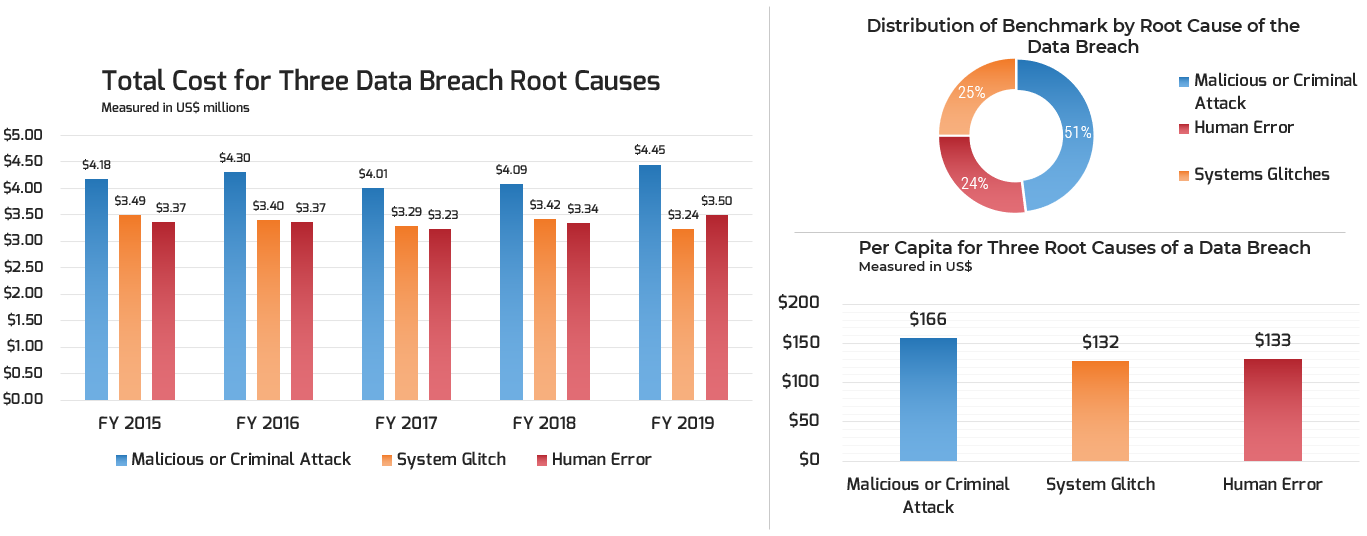
Source: Ponemon Institute, “2019 Global Cost of Data Breach Study”
An information security strategy can help you prepare for incidents
Organizations need to expect the inevitable security breach.
90%
of businesses have experienced an external threat in the last year.
50%
of IT professionals consider security to be their number one priority.
53%
of organizations claimed to have experienced an insider attack in the previous 12 months. 1
46%
of businesses believe the frequency of attacks is increasing. 2
Effective IT leaders approach their security strategy from an understanding that attacks on their organization will occur. Building a strategy around this assumption allows your security team to understand the gaps in your current approach and become proactive instead of being reactive.
Sources: 1 Kaspersky Lab, “Global IT Security Risks Survey”; 2 CA Technologies, “Insider Threat 2018 Report”
Persistent Issues
Evolving Ransomware
- Continual changes in types and platforms make ransomware a persistent threat. The frequency of ransomware attacks was reported to have increased by 67% in the past five years. 1
Phishing Attacks
- Despite filtering and awareness, email remains the most common threat vector for phishing attacks (94%) and an average of 3% of participants in phishing campaigns still click on them. 2
Insider Privilege and Misuse
- Typically, 34% of breaches are perpetrated by insiders, with 15% involving privilege misuse. Takeaway: Care less about titles and more about access levels. 3
Denial of Service
- The median amount of time that an organization is under attack from DDoS attack is three days.
Emerging Trends
Advanced Identity and Access Governance
- Using emerging technologies in automation, orchestration, and machine learning, the management and governance of identities and access has become more advanced.
Sources: 1 Accenture, “2019 The Cost of Cyber Crime Study”; 2,3 Verizon, “2019 Data Breach Investigations Report”
New threat trends in information security aren’t new.
Previously understood attacks are simply an evolution of prior implementations, not a revolution.
Traditionally, most organizations are not doing a good-enough job with security fundamentals, which is why attackers have been able to use the same old tricks.
However, information security has finally caught the attention of organizational leaders, presenting the opportunity to implement a comprehensive security program.
Cyberattacks have a significant financial impact
Global average cost of a data breach: $3.92 Million
Source: Ponemon Institute, “2019 Cost of a Data Breach Study: Global Overview”
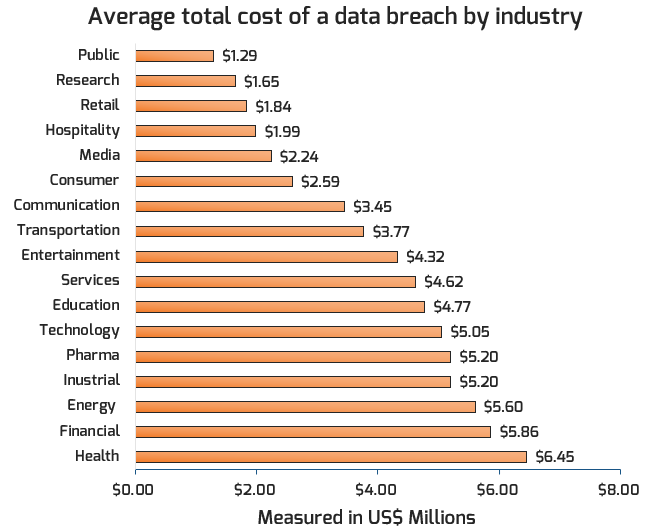
Primary incident type (with a confirmed data breach)
- Leading incident type is Denial of Service attacks (DoS), taking up to 70% of all incidents.
- When it comes to data breaches, we see that the use of stolen credentials leads to the most cases of confirmed breaches, accounting for 29%.
Personal records tend to be the most compromised data types, while databases tend to be the most frequently involved asset in breaches.
Source: Verizon, “2019 Data Breach Investigations Report”
Security threats are not going away
We continue to see and hear of security breaches occurring regularly.
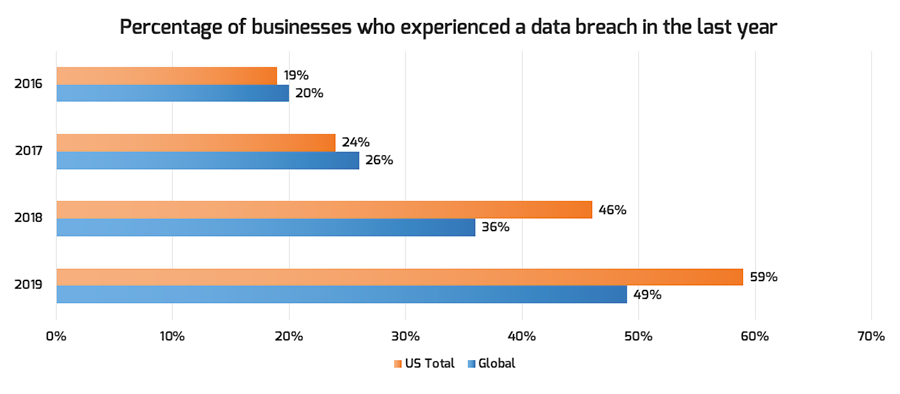
An attacker must be successful only once. The defender – you – must be successful every time.
Info-Tech’s approach
Maturing from reactive to strategic information security
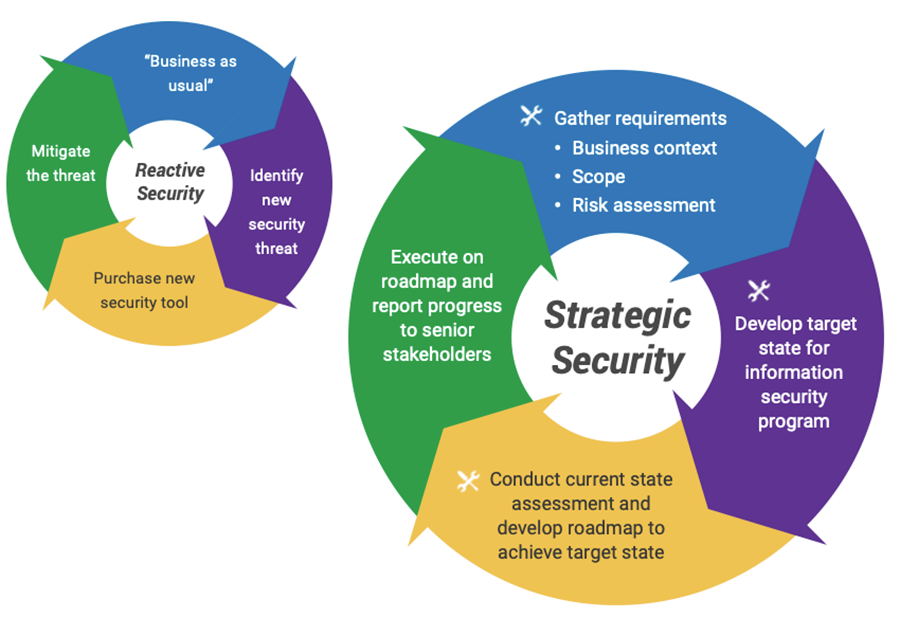
![]() Indicates Info-Tech tools included in this blueprint.
Indicates Info-Tech tools included in this blueprint.
The Info-Tech difference:
- A proven, structured approach to mature your information security program from reactive to strategic.
- A comprehensive set of tools to take the pain out of each phase in the strategy building exercise.
- Visually appealing templates to communicate and socialize your security strategy and roadmap to your stakeholders.
Info-Tech’s Security Strategy Model
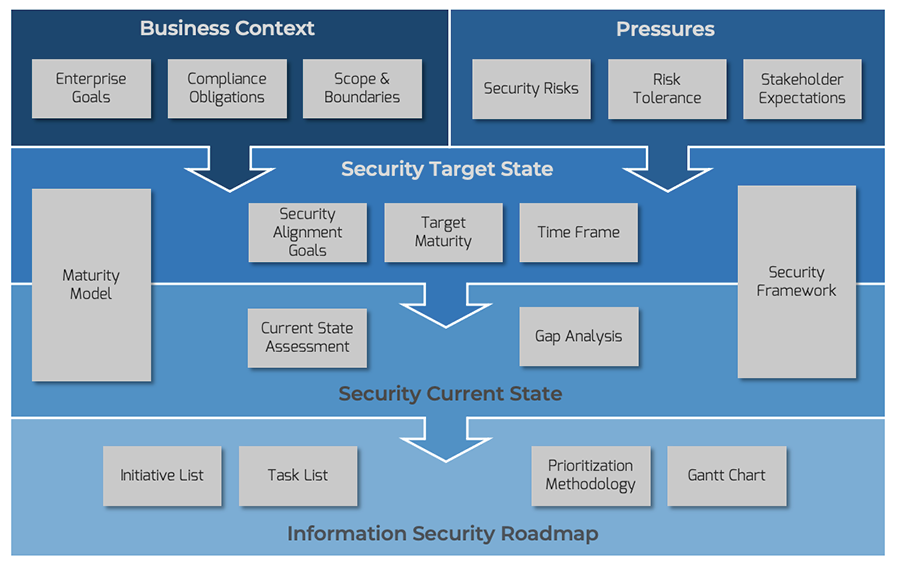
The Info-Tech difference:
An information security strategy model that is:
- Business-Aligned. Determines business context and cascades enterprise goals into security alignment goals.
- Risk-Aware. Understands the security risks of the business and how they intersect with the overall organizational risk tolerance.
- Holistic. Leverages a best-of-breed information security framework to provide comprehensive awareness of organizational security capabilities.
Info-Tech’s best-of-breed security framework
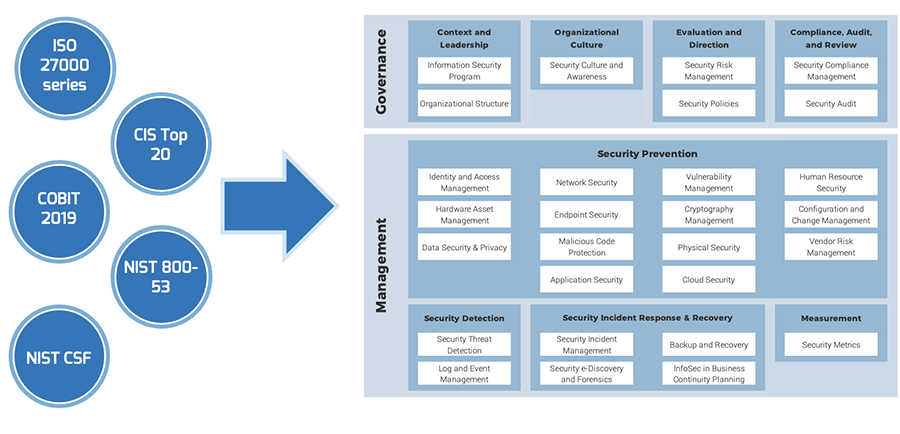
Info-Tech’s approach
Creating an information security strategy
|
Value to the business |
Outcome |
|
|---|---|---|
|
Best-of-breed security strategy |
Have documentation that paints a picture of the road to compliance. Integrate your framework with your risk tolerance and external pressures. |
Be ready for future changes by aligning your security strategy to security framework best practices. |
|
Address the nature of your current information security |
Eliminate gaps in process and know what is in scope for your security strategy. Learn what pressures your business and industry are under. |
Gain insight into your current state, allowing you to focus on high-value projects first, transitioning towards a target state. |
|
Highlight overlooked functions of your current security strategy |
Build a comprehensive security program that brings to light all aspects of your security program. |
Instead of pursing ad hoc projects, know what needs work and how to prioritize your pressing security issues. |
|
Create a tangible roadmap to your target state |
Create a plan for your future state of information security. Refer to and update your target state as your business needs change. |
Document your current progress and path forward in the future. Know your goals and requirements, codified in a living document. |
|
Use our prepopulated deliverables to fast track your progress |
Let Info-Tech do the work for you. With completed deliverables, have tangible documents to convey your business needs. |
A comprehensive set of deliverables with concrete, defensible data to justify any business changes. |
|
A living security strategy |
Pivot and change prioritization to meet the needs of your security deficits. |
Future-proof your security strategy for any contingency. |
The Info-Tech difference:
Evolve the security program to be more proactive by leveraging Info-Tech’s approach to building a security strategy.
- Dive deep into security obligations and security pressures to define the business context.
- Conduct a thorough current state and future state analysis that is aligned with a best-of-breed framework.
- Prioritize gap-closing initiatives to create a living security strategy roadmap.
_preview3848.jpg) Design and Implement a Business-Aligned Security Program
Design and Implement a Business-Aligned Security Program
 Build an Information Security Strategy
Build an Information Security Strategy
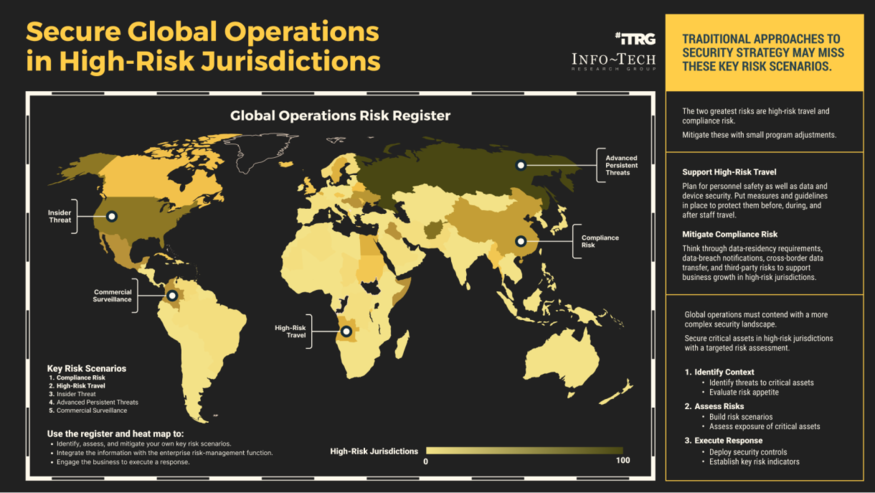 Secure Operations in High-Risk Jurisdictions
Secure Operations in High-Risk Jurisdictions
 Develop a Security Awareness and Training Program That Empowers End Users
Develop a Security Awareness and Training Program That Empowers End Users
 Build, Optimize, and Present a Risk-Based Security Budget
Build, Optimize, and Present a Risk-Based Security Budget
 Hire or Develop a World-Class CISO
Hire or Develop a World-Class CISO
 Fast Track Your GDPR Compliance Efforts
Fast Track Your GDPR Compliance Efforts
 Build a Cloud Security Strategy
Build a Cloud Security Strategy
 Identify the Components of Your Cloud Security Architecture
Identify the Components of Your Cloud Security Architecture
 Security Priorities 2022
Security Priorities 2022
 2020 Security Priorities Report
2020 Security Priorities Report
 Manage Third-Party Service Security Outsourcing
Manage Third-Party Service Security Outsourcing
 Select a Security Outsourcing Partner
Select a Security Outsourcing Partner
 Improve Security Governance With a Security Steering Committee
Improve Security Governance With a Security Steering Committee
 Dive Into Five Years of Security Strategies
Dive Into Five Years of Security Strategies
 The First 100 Days as CISO
The First 100 Days as CISO
 Determine Your Zero Trust Readiness
Determine Your Zero Trust Readiness
 Cost-Optimize Your Security Budget
Cost-Optimize Your Security Budget
 Assess the Viability of M365/O365 Security Add-Ons
Assess the Viability of M365/O365 Security Add-Ons
 Threat Preparedness Using MITRE ATT&CK®
Threat Preparedness Using MITRE ATT&CK®
 Build a Zero Trust Roadmap
Build a Zero Trust Roadmap
 Security Priorities 2023
Security Priorities 2023